infosec
Cyber Kill Chain
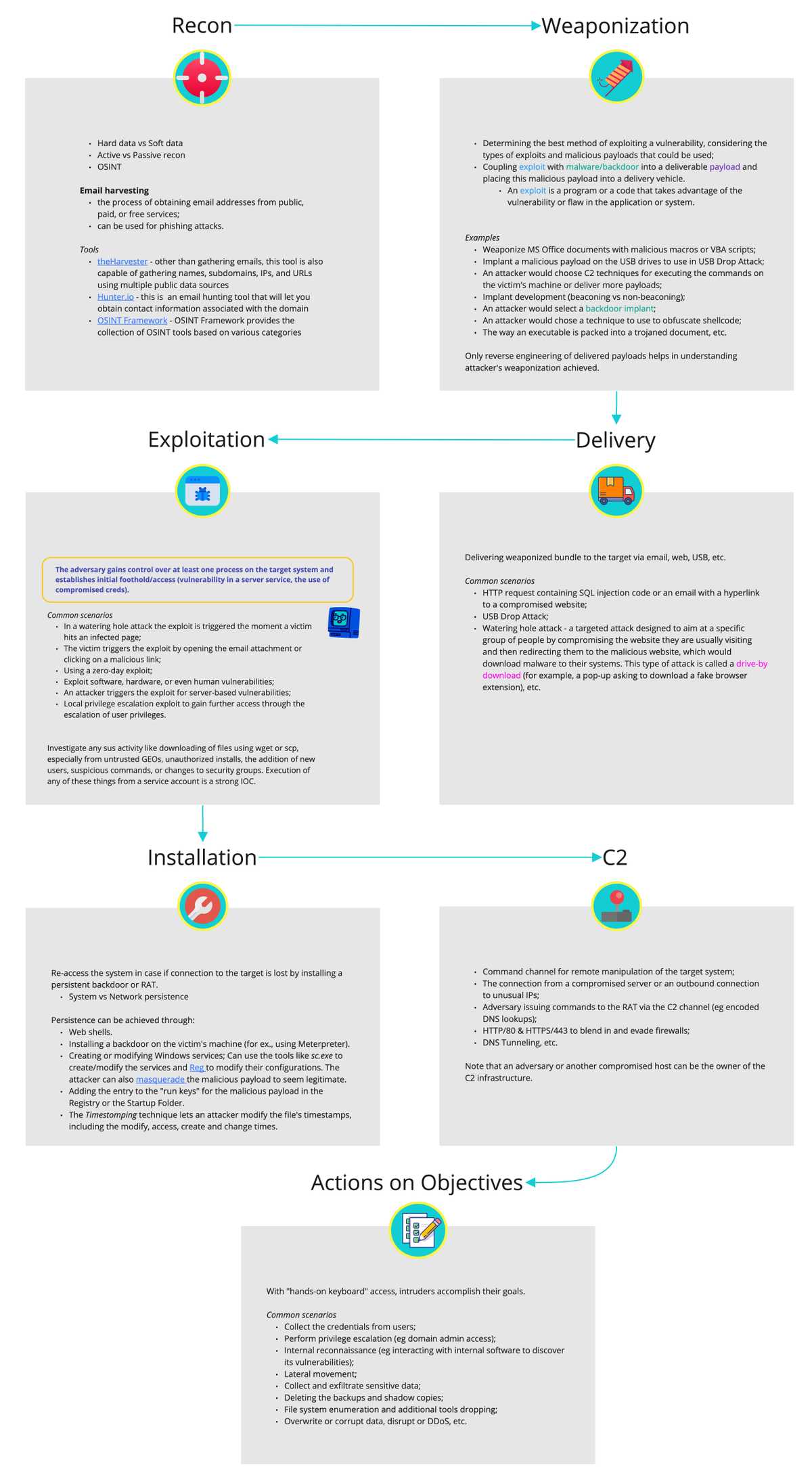
November 20, 2022Cyber Kill Chain = phases of attack. Incdent Response process is absctracted into incident cycle and cyber kill chain, where incidnet cycle is focused on the defender's actions and the cyber kill chain is focused on the adversary's actions. A single intrusion can be modeled as 7 phases of the Cyber Kill Chain: the targeting used (recon), the way in which the malicious payload is obscured (weaponization), the path the paylaod takes (delivery), the way the paylaod is invoked (exploitation), where the backdoor is hidden on the system (installation), the protocol used to call back to the attacker (C2) and adversaries actions on objectives/intent.